SOC 2 Compliance: 5 Key Measures to Protect Your Accounting Practice
Accounting practices occupy an uncomfortable position in the data protection landscape. As data controllers under UK GDPR, they bear full legal responsibility when vendors fail. A document management system breach or payroll processor leak lands squarely on the practice, not the supplier. The 2,970 data breaches reported to the ICO in the first quarter of 2024, up 21% from the previous year, underscore the scale of this challenge. For practices managing client tax records and financial statements, vendor security has shifted from technical concern to existential risk. SOC 2 compliance verification offers independent assurance that cloud platforms meet the rigorous standards accounting practices need.
The professional stakes extend beyond regulatory fines. Codes of conduct from ICAEW, ACCA and ICAS impose strict confidentiality obligations. When client data breaches occur through vendor failures, accountants face professional disciplinary action alongside legal penalties. Cloud adoption has accelerated dramatically, yet among UK financial services firms evaluating vendor risks only during onboarding, 68% suffered supply chain breaches in 2024. That figure drops to 32% for firms implementing continuous monitoring. The gap between adequate and inadequate vendor oversight has never been clearer.
Why Vendors Present Unique Risks
The data accounting practices handle commands premium prices on criminal markets. Tax records contain national insurance numbers and bank details. Payroll systems store employee financial data across multiple client companies. A single breach exposes information spanning dozens or hundreds of businesses. Small and medium-sized practices present particularly attractive targets because they hold valuable data whilst often maintaining weaker defences than larger firms. Only 14% of small businesses rate their cybersecurity as highly effective.
UK GDPR rules makes the legal position clear. Article 28 requires written contracts with data processors specifying security measures. Practices cannot delegate controller responsibilities. When vendors fail, the ICO looks first to the practice. Penalties reach £17.5 million or 4% of annual global turnover, whichever proves higher. Client compensation claims and professional indemnity increases compound the damage. Referrals dry up as word spreads through professional networks. Recovery takes years.
Understanding SOC 2 for Vendor Assessment
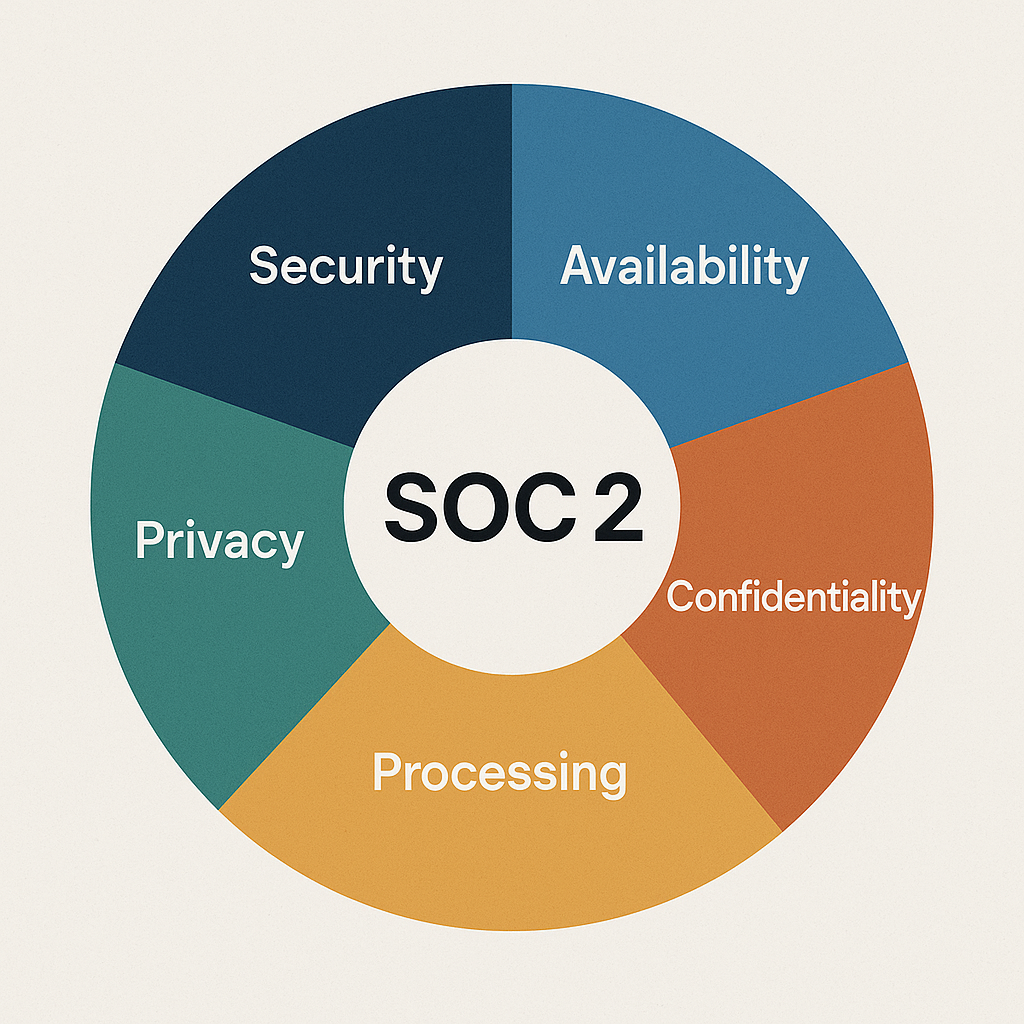
SOC 2 evaluates how service organisations manage five Trust Services Criteria established by the American Institute of Certified Public Accountants. Security is mandatory for all audits. The remaining four criteria, availability, processing integrity, confidentiality and privacy, apply based on services provided.
Availability ensures systems remain operational when needed. Processing integrity verifies calculations produce accurate results. Confidentiality protects sensitive information from unauthorised access. Privacy addresses how organisations handle personally identifiable information like national insurance numbers. For accounting software vendors, multiple criteria typically apply. Xero publishes SOC 2 Type 2 reports covering security, availability and confidentiality. Payroll processors need all five criteria to demonstrate comprehensive control over sensitive employee data.
The distinction between Type 1 and Type 2 reports determines practical value. Type 1 confirms controls exist at a specific point. Type 2 validates operating effectiveness over periods spanning three to 12 months. Type 2 reports demonstrate sustained security rather than momentary compliance. For practices satisfying Article 28 obligations, Type 2 reports provide evidence of reasonable due diligence in vendor selection.
Measure 1: Make SOC 2 Type 2 Reports Contractual Requirements
Before signing with cloud accounting platforms, document management systems or payroll processors, request current SOC 2 Type 2 reports. Independent verification demonstrates vendors maintain adequate controls to protect client data. The audit period matters considerably. Three-month coverage provides limited assurance compared with full-year audits. Reports older than 12 months offer minimal current value as security postures deteriorate when staff leave and systems change.
Verify auditor credentials carefully. Only certified public accountant firms issue SOC 2 reports. Auditors should hold information technology or information security certifications because SOC 2 audits differ fundamentally from traditional financial audits. Check the auditor appears on the AICPA website with relevant technology credentials. An unqualified auditor undermines the entire assurance process.
If critical vendors cannot provide SOC 2 reports, document alternative due diligence thoroughly. The ICO expects evidence of reasonable steps taken to verify vendor security. Request comprehensive documentation covering governance, risk oversight, personnel practices, information security, vendor management, data security, cyber controls, privacy standards and incident response. Self-reported documentation lacks independent verification. For vendors handling sensitive client data, SOC 2 compliance should be non-negotiable.
Measure 2: Focus on Exceptions, Not Summaries
Skip past marketing language to the exceptions section. Auditors document every instance where controls failed operating as designed. Clean reports with no exceptions indicate robust security. Multiple exceptions around access controls, encryption or incident response signal vulnerability requiring serious evaluation.
Management responses reveal as much as the exceptions themselves. Strong organisations acknowledge problems with concrete remediation plans and specific timelines. Weak responses deflect blame or offer vague future promises. Examine whether management demonstrates genuine commitment through documented timelines and resource allocation.
The complementary user entity controls section requires particular attention. These are security responsibilities falling to your practice rather than the vendor. Cloud accounting platforms might maintain excellent access controls but require you to enforce multi-factor authentication. Document management systems might encrypt data at rest but need you to implement secure password policies. Misunderstanding shared responsibilities creates gaps in data protection. The ICO will not accept vendor failures as excuses when you failed implementing required controls.
Check the auditor’s opinion letter thoroughly. Qualified opinions indicate significant control deficiencies. Unqualified opinions provide reasonable assurance controls operated effectively throughout the audit period. Adverse opinions represent serious concerns warranting immediate contract reconsideration.
Measure 3: Monitor Vendors Continuously
SOC 2 reports represent snapshots. Security conditions change constantly. The research demonstrates this starkly. Continuous monitoring reduces breach risk by more than half compared with onboarding-only verification. Most firms still fail implementing ongoing assessment despite the clear statistical evidence.
Build contractual requirements for vendors to notify your practice of material security incidents within 24 to 72 hours. UK GDPR requires reporting qualifying breaches to the ICO within 72 hours of becoming aware. You cannot meet this obligation when vendors delay notification. Set up automated alerts tracking vendor security news. Google alerts combining vendor names with breach, vulnerability and incident catch problems often reported in trade publications before formal notifications arrive.
Conduct quarterly security reviews beyond annual SOC 2 updates. Check whether vendors maintain adequate security staffing, apply patches promptly and address emerging threats. The reviews verify continued compliance with data processing agreements. Request updated SOC 2 reports annually without exception. Accountability principles demand demonstration of ongoing vendor compliance. Outdated reports provide no evidence of current security posture.
Measure 4: Negotiate Robust Data Processing Agreements
Standard vendor agreements favour vendors. They minimise liability whilst maximising flexibility to modify services. Data processing agreements must specify vendor security obligations in detail. Generic templates rarely satisfy requirements for practices handling sensitive financial data.
Explicitly designate vendors as data processors with clear obligations around security measures, processing limitations and breach notification timelines. Specify that client data remains your property and your clients’ property. Define data return and deletion procedures for contract termination with specific timelines and verification methods. When processing relationships end, deletion or return requirements create ongoing liability if ignored.
Security requirements should reference maintaining SOC 2 compliance throughout the contract term. Include audit rights allowing verification of vendor security controls. Some vendors resist audit clauses. Accountability principles require demonstration of vendor compliance. Audit rights represent essential evidence for ICO investigations or client inquiries about data protection measures.
Liability provisions require careful negotiation. Vendors typically cap liability at annual contract value. This proves inadequate covering actual breach damages. ICO fines can reach up to £17.5 million or 4% of turnover. Client compensation and professional indemnity claims compound losses. Negotiate higher liability caps specifically for data breaches. Require vendors maintain cyber insurance covering minimum thresholds appropriate to your client data volume.
Measure 5: Prepare Vendor Breach Response Procedures
Vendor breaches remain possible despite rigorous vetting. Response procedures determine whether incidents trigger ICO enforcement or demonstrate reasonable compliance efforts. Most UK businesses lack adequate incident response plans.
Designate a response team including senior leadership, IT personnel or managed service providers, legal counsel familiar with UK GDPR, and communications staff prepared for client notifications. Identify external forensic specialists and understand cyber insurance coverage before incidents occur. Documented procedures demonstrate preparedness under accountability principles.
Response plans must outline decision criteria for determining whether vendor breaches meet ICO reporting thresholds. Prepare communication templates for regulatory notifications and client disclosures. Professional body codes require prompt client notification of confidentiality breaches. These dual obligations demand immediate action when vendor security incidents occur.
Establish detection procedures beyond waiting for vendor notifications. Monitor for unusual activity in vendor-connected systems including unexpected data access patterns, configuration changes or performance degradation. When Marks & Spencer suffered a cyberattack in April 2025, attackers bypassed contractor defences through social engineering. The retailer lost online functionality for six weeks with estimated losses reaching £300 million, demonstrating how quickly vendor security failures cascade into operational catastrophe.
Document all vendor security incidents, even minor ones not requiring ICO reporting. This evidence demonstrates ongoing monitoring efforts during investigations. Professional indemnity insurers increasingly request documentation of vendor security procedures when underwriting practices. Comprehensive records support both regulatory compliance and insurance coverage.
Building Competitive Advantage Through Vendor Oversight
Vendor security represents professional responsibility under codes governing UK accounting bodies. The statistics reveal urgency. Continuous monitoring cuts breach risk by more than half. Yet most firms fail implementing ongoing assessment. This gap between best practice and common practice creates both vulnerability and opportunity.
Practices demonstrating rigorous vendor oversight attract clients increasingly concerned about data protection. Larger businesses subject to their own regulatory requirements actively seek accounting partners documenting comprehensive vendor risk management. When competing for new clients, documented SOC 2 verification processes and robust data processing agreements differentiate your practice from competitors treating vendor security as afterthought.
The measures outlined demand significant time investment. Smaller practices may not have dedicated IT security staff, but the cost of strong vendor management is minor when compared to the impact of a breach. A single serious vendor incident can destroy long-built client relationships and expose practices to ICO fines, professional disciplinary action, and legal liability. Professional indemnity claims increasingly cite vendor security failures as contributing factors.
Protecting client data is a core professional responsibility for UK accountants. The trust clients place extends across the entire technology ecosystem supporting their relationships, and this responsibility cannot be delegated. Rigorous SOC 2 verification shows regulators and professional bodies that reasonable steps are being taken when selecting and monitoring vendors. As cloud adoption grows, firms that build strong vendor risk management practices now safeguard both their clients and their professional reputation.






